+61 (0) 481355646
reply@assureditinfra.com.au
Victoria, 3029 Australia
Follow On:


I started my journey in to the Cloud Security Engineering space, Been looking in to several enterprises and their existing GCP Infrastructure/s from Cloud Security Architecture perspective — noticed some of the fundamental issues & gaps with their existing Cloud Architecture and Cloud Security Posture.
As I understood the gaps to some extent [still long way to go and experience many more business cases and scenarios though] – It has been going through my mind for couple of months now that ‘Why don’t I write and simplify it for easy and quick reference for everyone desired?’ to have a look and take this further to enhance their Cloud Security Posture from the very beginning of their Cloud Journey
and
The Time has come now to sit and start writing it down. Thanks to X’mas vacations/holidays which helps bit of free mind and enables the idea/s to flow easily. I prefer sitting at one-go and finish it in one-sitting from the very start to end irrespective of the time it takes to complete, that helps me to keep that continuous flow of thoughts in to my writing.
That’s me and Only Me!
The Perfect time to trigger my idea to blog here which aims to give initial *must* considerations for any GCP Cloud Project or Projects for your organisation
Fundamental issue I’ve noticed is that everything is jam-packed in to one single folder and isolation is existing only between the projects but within the same folder which leads to a potential attack surface
To avoid this, Channelize your resources and following ‘resource hierarchy’ allows you to map your organisation’s (operational) structure to Google Cloud and thus allow you to manage them in an organised manner
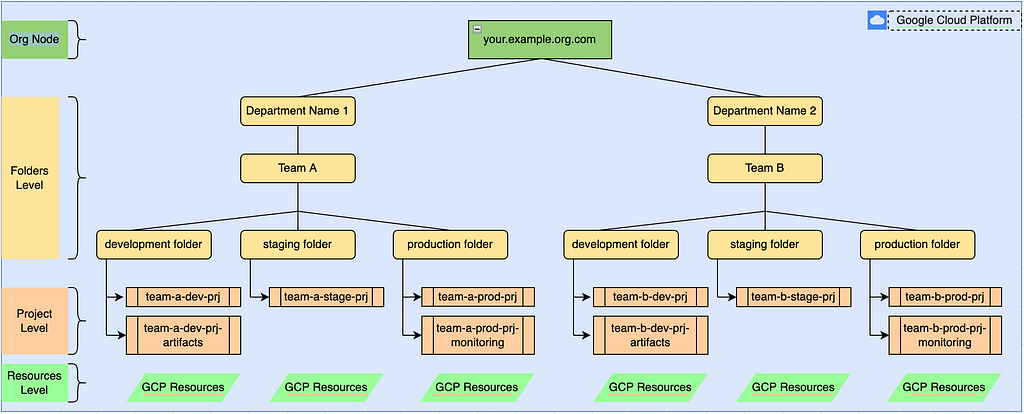
The Org Node aka ‘Organisation’ helps to provide central visibility and control over all the resources under that Organisation node
Folders help to create isolation between different teams or departments under the organisation. Folders can be further split in to sub-folders based on your business needs and there is no restriction on folder levels.
The bottom layer is the ‘Project’ level. Projects help contain GCP resources which help constitute your application/s. Projects can contain resources spread across multiple regions and geographies. Best Practice is to have one project per application per environment. For eg., if you’ve 2 applications ‘A’ and ‘B’, with a development, staging and production environment, you would have 6 projects in total such as A-dev, A-stage, A-prod and B-dev, B-stage, B-prod. This segregation helps in isolating the environments from each other so that changes in one project/env do not accidentally impact other project/env and also helps provide better access control too
2. Implement IAM [Identity and Access Management] as the standard
In a nut shell, most common issues found are like using ‘individual’ accounts instead of ‘groups’ to grant access to specific Google Cloud resources and fully ignoring the basic security principle of ‘least privilege’
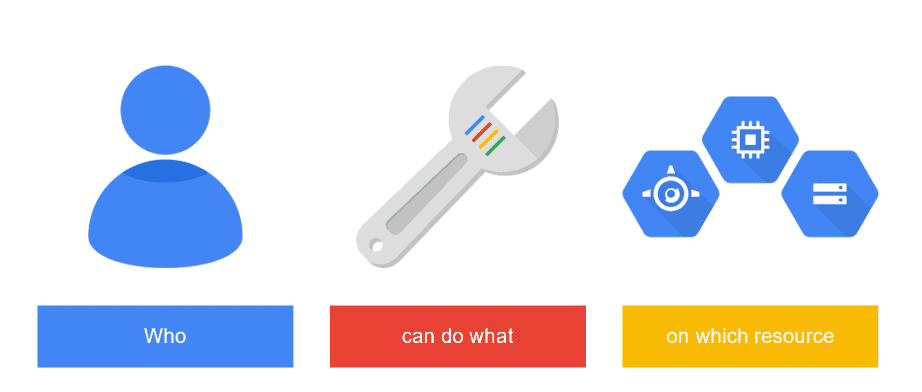
To avoid this, follow the recommended IAM best practices such as:
3. Custom Network and Network Security —Think and Design Early
To be frank, the issues I noticed under this section are like eye-openers as I couldn’t believe my eyes when I first looked at it.
You know what — People are using ‘Default’ Networks. Just not that but also ‘Default’ firewall rules which are unbelievably true from my perspective. You cannot start worse than this ;>(

Let me simplify the bare minimum things to start considering from the beginning
4. Securing your Applications and Data
Google Cloud has many wonderful Products and Services which helps your applications and data to be more secure and safe in addition to the scale you are looking for. Start using them to get the best benefit
Some of the major gaps I’ve noticed with my different enterprise GCP foundation assessments are like No VPC Service Controls in place, No usage of Secret Manager at all, Poor Cloud SQL Security Configuration, Cloud Functions running with abnormalities and Steps not taken for Application Scalability and Security
Let me simplify ‘why’ you need to consider them from the get go:
5. Logging, Monitoring and Operations
Enterprises typically run multiple applications and processes and often across different platforms. Logging and Monitoring of these applications from Operations perspective is a key element which helps track the health of the applications. To help with these business needs, google cloud has Cloud Logging and Cloud Monitoring services to manage logging, monitoring, debugging, tracking, profiling and many more.
General tendency I’ve noticed during my assessments is that the business users are unaware these services and their benefits. In this blog, I’ll try to highlight ‘why’ it is beneficial to make use of these services to the best possible

6. Billing and Management
Even though this sounds very critical as it deals with $, it was surprising to see in some cases that this section has been handled in a least effective manner.
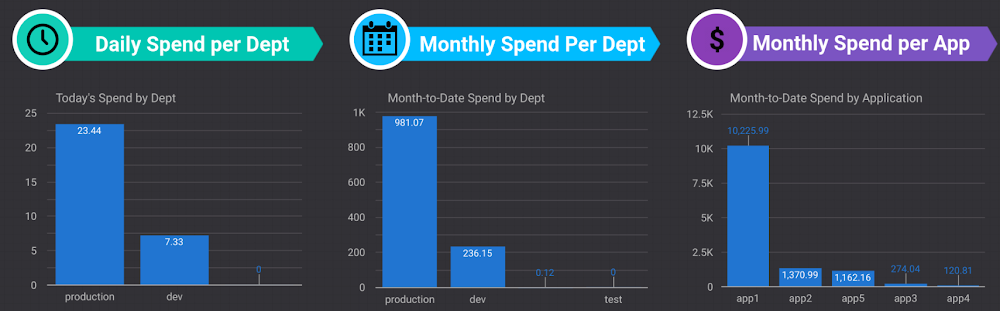
Fundamentally, enterprises should take steps to understand ‘how each of these google cloud resources are charged’, ‘how they can setup a billing management controls’ and then plan for their capacity requirements by implementing cost controls and build centre of excellence over time
Budget Alerts are very critical for control and monitoring of the $$$ spent and implement ‘Labelling’ where ever applicable for easy tracking and isolation in breaking down the costs. These alerts help in the case of any excessive spending due to any malicious activity or attacks such as DDoS etc.,
In order to build a centre of excellence, it is a good practice to nominate Google Cloud Experts and Champions in your team/organisation. A range of training and certification options are available to help nominated champions to grow in their area and build their expertise. Teams can stay up to date on the latest news, announcements and customer stories by following the Google Cloud Blog
That’s it for now.
As you know, the topic is very huge and we can go on and on and on as there are too many things to consider and highlight in each of the sections above ….
but with this blog, I wanted to touch upon bare minimum things to start eyeing from the day one and start building it more and more securely as you progress.
Hope this information finds useful.
Thanks for taking time to read!